Detailed Breakdown
The Problem:
Illegal robocalling had reached epidemic levels, eroding customer trust in voice communication and leading to significant regulatory pressure to do something. In fact, unwanted robocalls were the number one complaint the FCC received from consumers each year. Passed by Congress, the TRACED (Telephone Robocall Abuse Criminal Enforcement and Deterrence) Act provided the FCC with the authority and tools to begin the fight against illegal robocalls. The first objective the FCC mandated: Voice carriers must implement STIR/SHAKEN by a strict deadline, a complex technical challenge with no existing blueprint for any highly complex network infrastructure.

The Opportunity:
Beyond mere compliance, this was an opportunity to restore customer confidence, differentiate our service by offering enhanced security, and build a foundational framework for future identity-based voice products. Successfully implementing this would not only protect our customers but also position us as a leader in network security.
Target Persona:
The primary focus was on three groups:
• Our internal network architects and engineers who needed to implement the changes across dozens of disparate systems without causing service interruptions.
• All of our service provider customers (both enterprise and wholesale) who were ultimately the beneficiaries of participating in a more secure calling experience.
• Our carrier interconnects with whom we ultimately would be sending and receiving these new identity headers.
Key Insights:
Early analysis revealed that a "one-size-fits-all" solution was impossible. Call flows for our IP products varied widely depending on which legacy network hardware the calls came through. We also discovered through collaboration with other carriers that interoperability of the new SIP Identity Header would be the single biggest point of failure if not handled proactively!
Product Vision:
Create a seamless, secure, trusted voice network and lay the foundation for future trusted voice services.
Strategic Roadmap:
The project was broken into phases, prioritized by network segments with the highest traffic and risk. This phased approach allowed for proper risk management and allowed time for program adjustments as needed.
• Phase 1 focused on our core IP network.
• Phase 2 addressed complex interconnection challenges with other carriers.
• Phase 3 tackled legacy network gateways and end of life equipment.
Solution:
The solution involved deploying both an Authentication Service (STI-AS) and Verification Service (STI-VS). These services would interact with our core network elements to sign outbound calls with the proper attestation level (A, B, or C) and verify already-signed inbound calls destined to our customers and their end user subscribers.
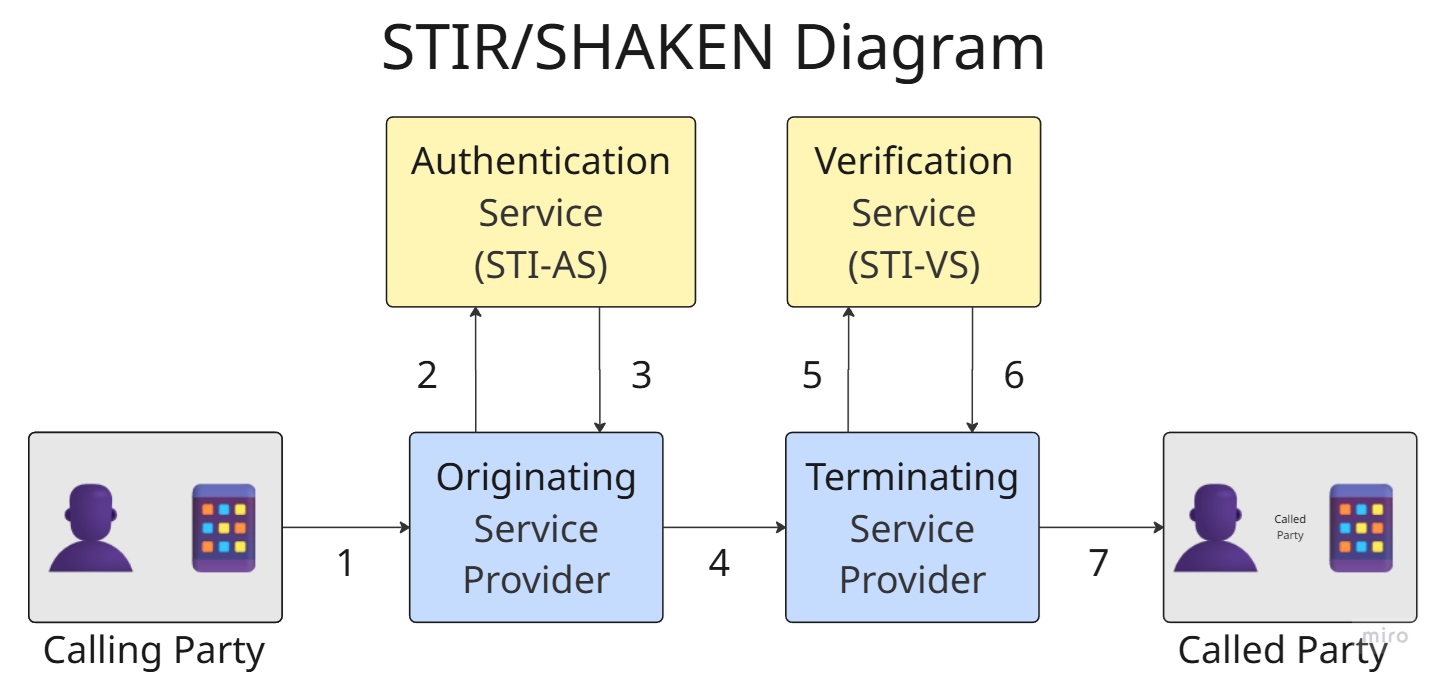
Key Features:
• Signing of outbound calls with A, B, C attestation.
• Verification of inbound call signatures.
• Centralized policy engine for routing and handling of unverified calls.
• Interoperability testing and certification with major carrier partners.
• Analytics dashboard for monitoring signed/unsigned traffic and attestation levels.
Process & Collaboration:
This was a massive cross-functional effort. I worked daily with Architecture & Engineering to ensure regulatory requirements were properly represented in High Level Design (HLD) technical specifications. I collaborated with Marketing and Sales to develop external communications, and with our legal team to ensure every step met the FCC's interpretation of the law. Regular syncs with other Tier 1 carriers were critical for solving interoperability challenges.
Results & Impact:
We successfully met the FCC deadline, signing over 95% of all IP-generated traffic within the first month and positioned us as one of the first Tier 1 carriers to be fully compliant.
Reflection:
The biggest lesson learned for me was that I could have set more realistic expectations (both internally and externally) of what STIR/SHAKEN was supposed to accomplish. While the end goal for everybody is to eliminate illegal robocalls, this solution had a general misconception that it was going to solve the problem in its entirety. Ultimately, those who were deeply involved understood that this was just the first step in what would need to be many steps in order to start chipping away at the whole problem.